

Cybersecurity is an ever-evolving field, and as new solutions are introduced to better detect and defend against cyberthreats, attackers in turn need to adapt their tactics to try and evade those solutions. For example, Barracuda threat analysts have recently identified a rise in phishing attacks that leverage trusted content creation and collaboration platforms popular with schools and designers as well as businesses.
The platforms are used by millions of people around the world and are designed for easy and open collaboration and creativity. Users trust the platforms’ tools and attackers are exploiting this to distribute malicious content while evading detection.
The analysts found that attackers are sending out emails from these platforms, featuring legitimate-looking posts, designs, and documents, but with embedded phishing links.
If an email recipient interacts with these links, they are often directed to fraudulent login pages or other deceptive sites intent on stealing sensitive information, such as login credentials and personal data.
The analysts believe this approach is part of a broader shift in phishing tactics, where attackers target popular, reputable platforms to implement their attacks, increasing the chances of success and evading detection.
The exploitation of trusted tools also poses a greater challenge for the security professionals and email protection technologies tasked with protecting users.
Phishing attacks leveraging educational technology
The analysts found several phishing attacks leveraging an online collaboration tool widely used in educational settings. The platform allows students to create and share virtual boards or “walls” where they can post and organize several types of content.
Cybercriminals are leveraging the platform’s post walls to send emails with embedded phishing links or URLs. In one example seen by the analysts, the platform is used to host voice mail phishing links. Once the user clicks the button to play the voice mail, it takes them to another link, which redirects them to a fake Microsoft login page designed to capture and steal their login credentials.
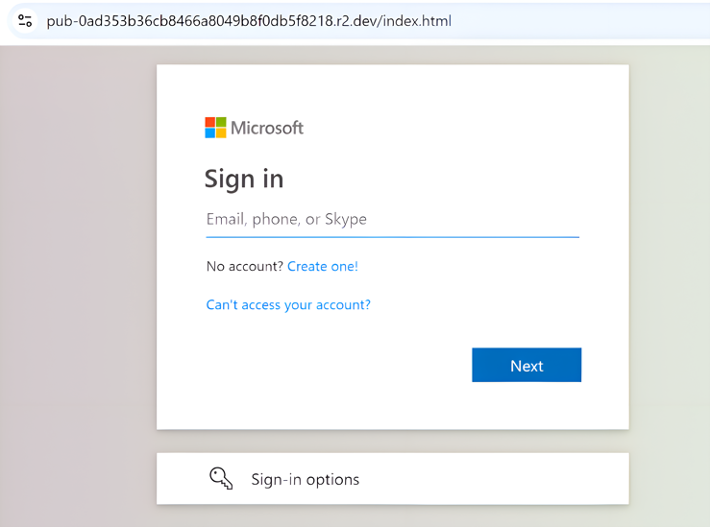
In another example, the attackers trick the user into clicking a link to view all files and project details before a supposed bidding deadline.
When the victim clicks on the link, they are redirected to a shared file link that seems to be a secure document. This ultimately takes them to a phishing site where their credentials are stolen.
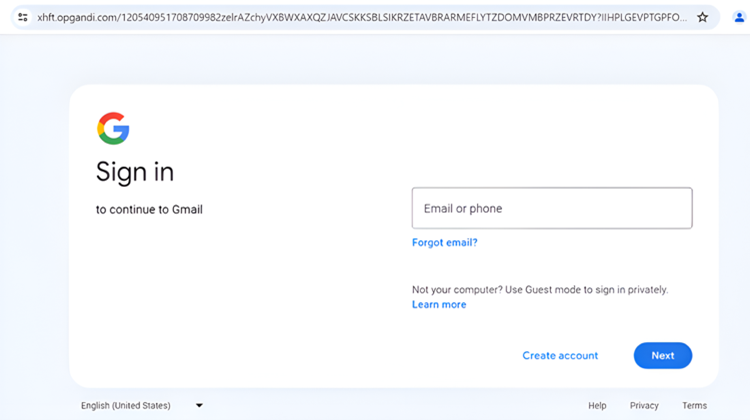
Phishing attacks leveraging a graphic design platform
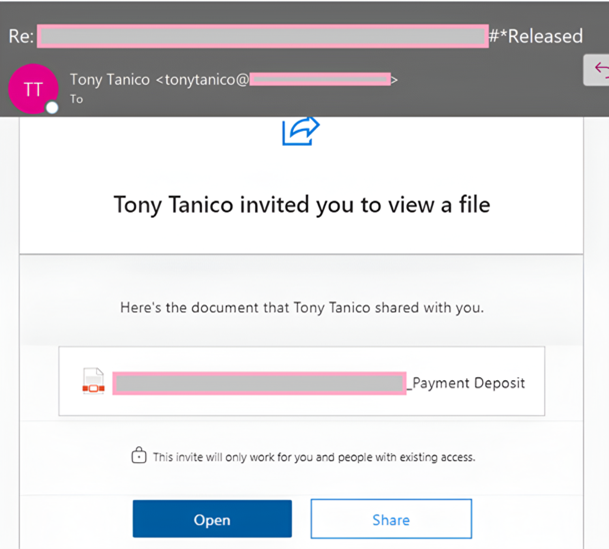
Barracuda’s analysts identified a phishing attempt leveraging a popular online graphic design platform. The emails sent from the platform involve what looks like a legitimate file sharing invitation from Microsoft 365. However, it takes victims through a series of links to a page designed to steal their credentials.
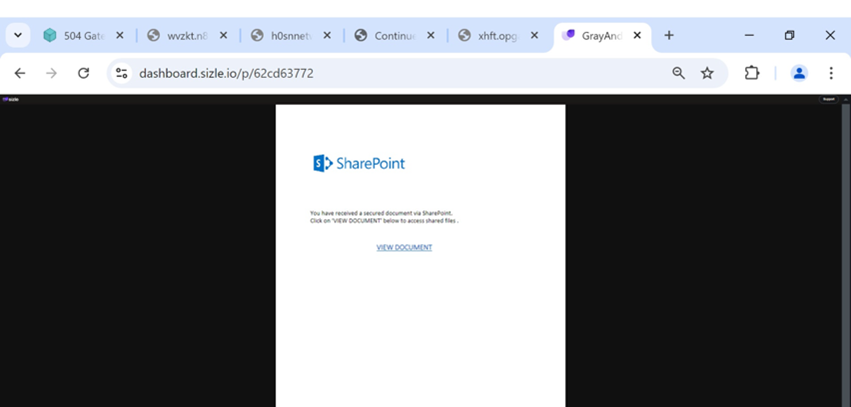
Phishing attacks leveraging a business file sharing and tracking platform
The third example seen by the analysts involved an online platform designed to streamline the creation, sharing, and tracking of documents. Unlike the other two platforms leveraged for phishing, this platform is mainly focused on business professionals.
The analysts found several fake “File Share” notifications hosted on the site and included in emails, which are designed to take victims to a page that will steal their login credentials.
Conclusion
As mentioned above, the increase in phishing attacks leveraging trusted content creation and collaboration platforms highlights a shift in cybercriminal tactics towards the misuse of popular, reputable online communities to implement attacks, evade detection and exploit the confidence that targets will have in such platforms.
It is vital that for individuals and organizations, including educational institutions, remain vigilant and implement robust security measures that can detect and adapt to evolving threats.
For example, individuals need to be wary of clicking on links in unsolicited emails, or in messages from people they don’t know. Other potential red flags include suspicious calls to action, and unexpected or illogical landing sites from links they receive, such as a service that isn’t provided by Microsoft asking for Microsoft logins.
In terms of security solutions, email protection solutions that feature multilayered, AI- and machine-learning-powered detection prevent these types of attacks from reaching user inboxes. This should ideally include sophisticated “intent” analysis, capable of intelligently scanning all URLs in emails for phishing threats.
This article was originally published at Barracuda Blog.
Photo: Skrypnykov Dmytro / Shutterstock
This post originally appeared on Smarter MSP.


