

 In this edition of the Email Threat Radar, Barracuda threat analysts highlight several notable email-based threats identified over the past month. These threats were designed to evade detection and increase the chances of success, and they targeted organizations around the world, including:
In this edition of the Email Threat Radar, Barracuda threat analysts highlight several notable email-based threats identified over the past month. These threats were designed to evade detection and increase the chances of success, and they targeted organizations around the world, including:
- Email attacks targeting victims with toxic calendar invites
- Phishing kits abusing a trusted file-sharing platform
- Voicemail phishing returning after several months of decline
Toxic calendar invites are yet another email trap for victims
Threat snapshot
Barracuda’s threat analysts have spotted the Sneaky 2FA phishing kit distributing poisoned calendar invites in an attack designed to steal user credentials.
ICS (iCalendar) attachments work across different platforms like Google Calendar, Microsoft Outlook and Apple Calendar. This compatibility makes ICS (.ics) files popular for scheduling events, meetings and appointments between organizations. They are particularly useful for virtual meetings, as they can contain URLs for video calls or related documents.
In the attack seen by Barracuda threat analysts, the email body is empty, and there is just a link to an ICS file that appears to be a legitimate calendar invite. The file contains some event details as well as a phishing link that claims to take the recipient to an unpaid invoice.
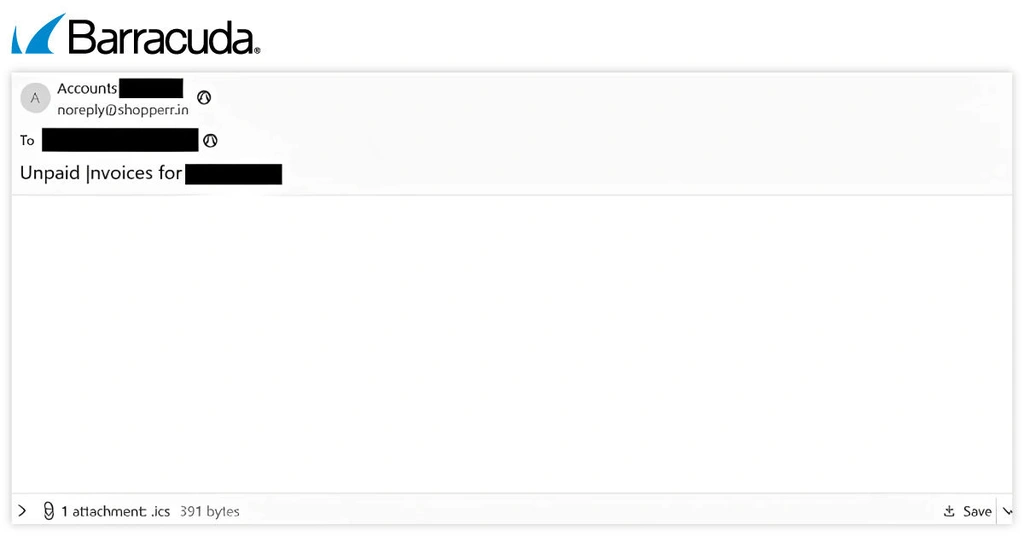
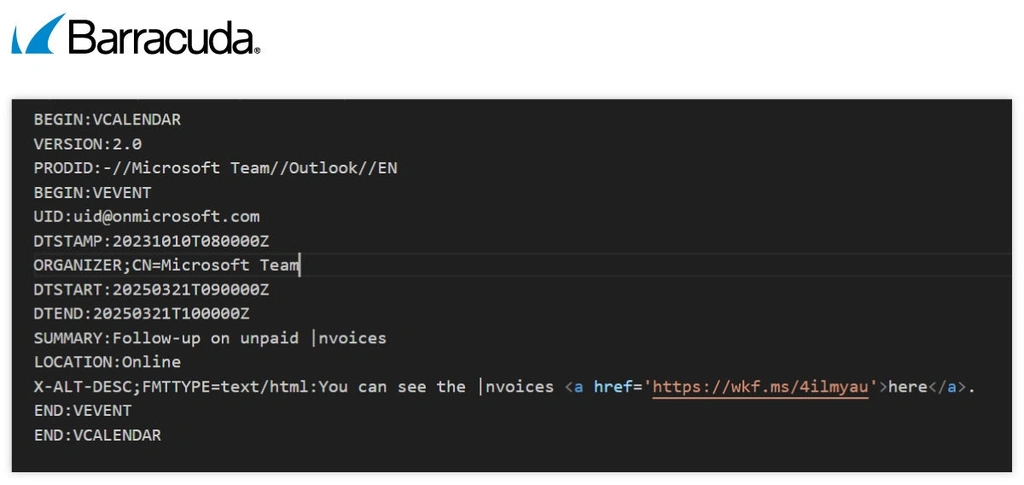
When the recipient opens the invitation, there is a link pointing to the legitimate Monday platform where the phishing content is hosted.
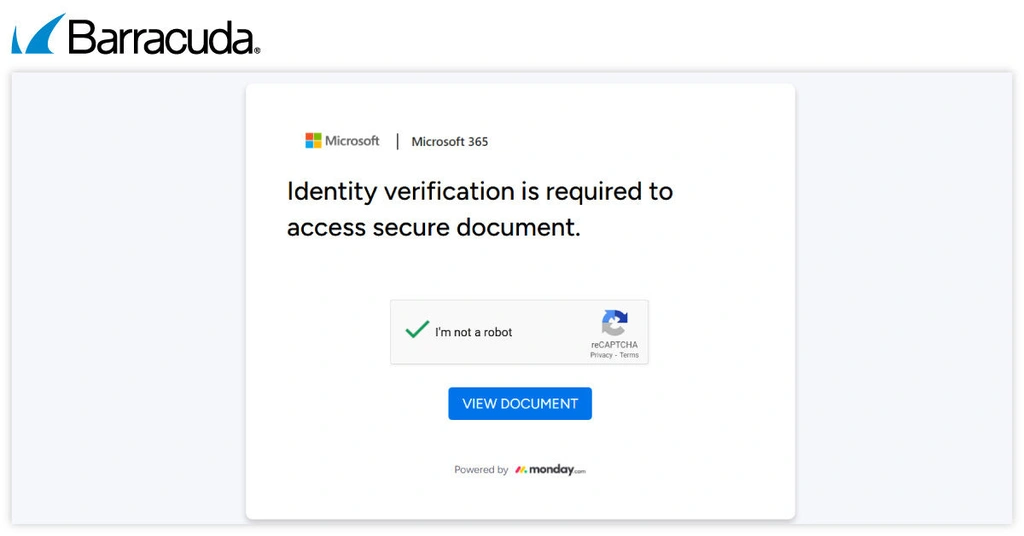
The victim is presented with a CAPTCHA verification and needs to click “view document,” which redirects them to a phishing page designed to steal their Microsoft credentials.
Signs to look for
- Any of the following should raise an alarm:
- A meeting invite that you are not expecting.
- From someone you don’t know or don’t hear from often.
- To discuss something you are unaware of.
- Additionally, if there is no context or covering message, it should be treated with caution. Report the message to your security team and check with the sender directly if appropriate to verify if the message is legitimate.
- The use of calendar invites in phishing attacks is on the rise, with several reports of Google calendar invites being spoofed in phishing campaigns.
- Since ICS files are often considered harmless and not all security tools can spot malicious invites, this represents a new opportunity — for a while at least — for attackers to bypass security controls and snare victims.
Phishing kits abuse ShareFile to launch hundreds of attacks
Threat snapshot
Barracuda’s threat analysts have spotted several hundred attacks by notorious phishing kits taking advantage of the legitimate ShareFile document-sharing platform.
The kits are hosting fake login forms on ShareFile and sending ShareFile URLs to potential victims.
This isn’t the first time that Barracuda’s threat analysts have found phishing content hosted on ShareFile, but its use by prominent phishing-as-a-service (PhaaS) platforms is a new development. This tactic appears to be the latest in a long line of adaptations by PhaaS groups to evade detection, increase stealth and ensure the survival of phishing campaigns.
The kits hosting content on ShareFile are the advanced and rapidly evolving Tycoon 2FA and Mamba 2FA. Barracuda recently reported on the behavior of Tycoon 2FA and other rising PhaaS platforms. Mamba 2FA follows a similar approach.
Mamba 2FA — another PhaaS ‘Most Wanted’
Mamba 2FA targets Microsoft 365 users and can intercept one-time passcodes and authentication cookies to bypass multifactor authentication.
Evasion techniques include using proxy servers and short-lived, rotating phishing links to avoid blocklisting. Attackers also use HTML attachments with junk content to bypass detection by security tools. Additionally, they employ sandbox detection, redirecting unwanted traffic—such as security scanning tools—to unrelated sites like Google 404 web pages.
The ShareFile attack method
The phishing emails usually impersonate SharePoint or DocuSign and feature a file-sharing notification. The included link directs recipients to a fake document hosted on ShareFile
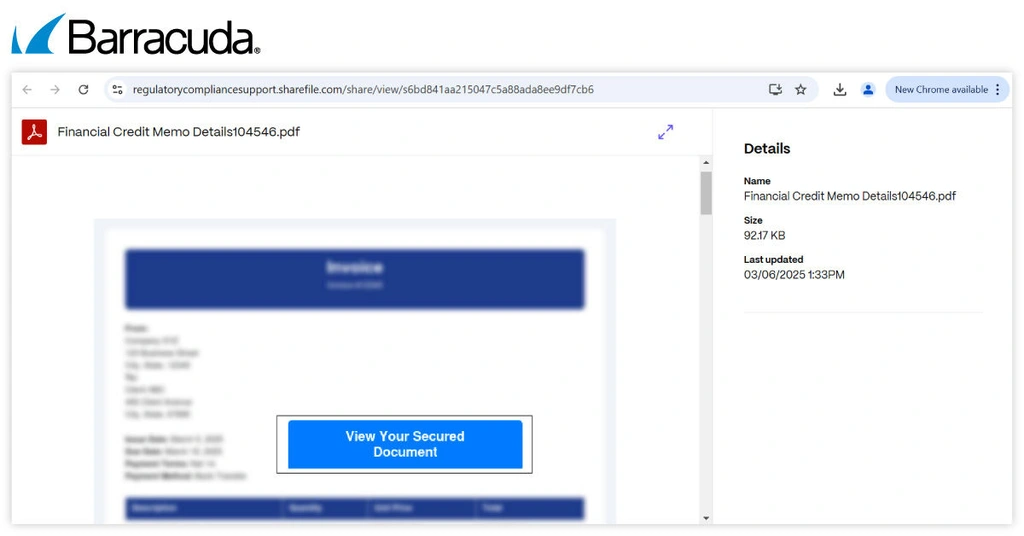
Because the email includes a legitimate ShareFile URL, the message doesn’t flag any security concerns. Recipients trust the platform, which makes them more likely to click on the link. As a result, they are also more inclined to enter the requested login da
Signs to look for
- As mentioned, an unexpected email from someone you don’t often hear from should raise suspicion. Additionally, if the topic is unusual for you, it should sound alarm bells.
- As should an email from ShareFile when your organization doesn’t generally use ShareFile.
- Report the message to your security team. If appropriate, check with the sender directly to verify whether the message is legitimate.
- If the email includes a link directing you to a Microsoft or Google login page, check that it is a legitimate login page. Avoid entering your credentials if you suspect the page might be fake or malicious.
Voicemail-based form phishing on the rise again
Threat snapshot
Since February, Barracuda threat analysts have observed a rise in voicemail-based email phishing, or vishing, attacks. This increase follows a period of decline. The attackers pose as voicemail alerts and direct recipients to online forms hosted on legitimate platforms like Monday and Zoho. On these forms, they prompt users to enter their credentials.
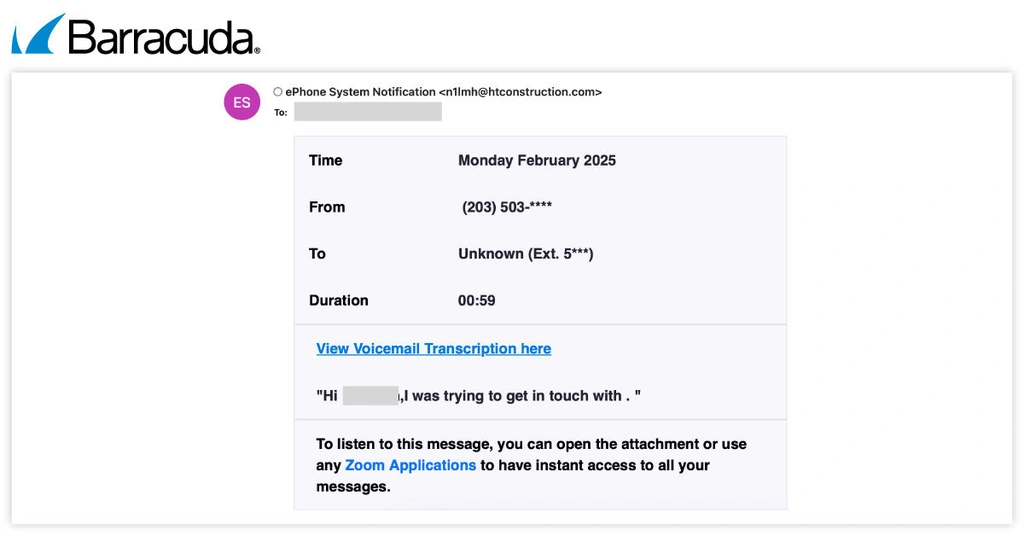
Other recently detected vishing attacks involved Mamba 2FA and Tycoon 2FA. One of these attacks used the professional social media platform LinkedIn as part of the URL redirect.
Signs to look for
- As above, unexpected or unsolicited messages—with unusual senders, content, or context—should raise a red flag for recipients. Always verify the source if it really does seem genuine.
- Another red flag is any pressure to act or respond quickly or any kind of veiled threat.
How Barracuda Email Protection can help your organization
Barracuda Email Protection offers a comprehensive suite of features designed to defend against advanced email threats.
It includes capabilities such as Email Gateway Defense, which protects against phishing and malware, and Impersonation Protection, which safeguards against social engineering attacks.
Additionally, it provides Incident Response and Domain Fraud Protection to mitigate risks associated with compromised accounts and fraudulent domains. The service also includes Cloud-to-Cloud Backup and Security Awareness Training to enhance overall email security posture.
Barracuda combines artificial intelligence and deep integration with Microsoft 365 to provide a comprehensive cloud-based solution that guards against potentially devastating, hyper-targeted phishing and impersonation attacks.
Further information is available here.
This article was originally published at Barracuda Blog.
Photo: fizkes / Shutterstock
This post originally appeared on Smarter MSP.

