
 A new commercial mobile spyware platform, ZeroDayRAT, is being promoted to cybercriminals on Telegram as a tool that provides full remote control of compromised Android and iOS devices. Researchers at mobile threat hunting company iVerify describe it as a “complete mobile compromise toolkit,” capable of data theft, real‑time surveillance, and financial fraud. Review the Cybersecurity Threat Advisory to learn more and mitigate your risk.
A new commercial mobile spyware platform, ZeroDayRAT, is being promoted to cybercriminals on Telegram as a tool that provides full remote control of compromised Android and iOS devices. Researchers at mobile threat hunting company iVerify describe it as a “complete mobile compromise toolkit,” capable of data theft, real‑time surveillance, and financial fraud. Review the Cybersecurity Threat Advisory to learn more and mitigate your risk.
What is the threat?
ZeroDayRAT is a cross‑platform mobile spyware/remote access Trojan (RAT) that provides persistent, full-featured access to infected smartphones and tablets. The attacker dashboard displays device metadata including:
- Device model
- OS version
- Battery status
- SIM details
- Country
- Lock state

Dashboard overview – Source: iVerify
From there, operators can access extensive logging, tracking, and real‑time control capabilities.
Passive surveillance and logging
ZeroDayRAT can:
- Log app usage and activity timelines
- Capture SMS messages
- Track notifications from messaging, email, and financial apps
- Enumerate registered accounts for potential brute-force or credential-stuffing attacks
Location tracking
If GPS permissions are granted, the platform can:
- Track victims in real time
- Display their location on Google Maps
- Maintain full location history for movement analysis
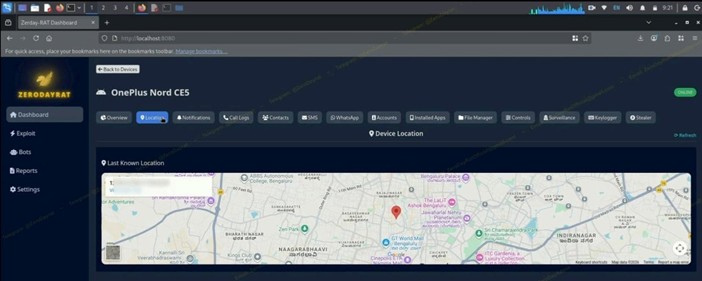
Tracking the victim in real time – Source: iVerify
Active, hands-on operations
Operators can:
- Activate front/rear cameras for photos or video
- Activate the microphone for live audio capture
- Record the screen, exposing app content, login prompts, MFA challenges, typed information, and more
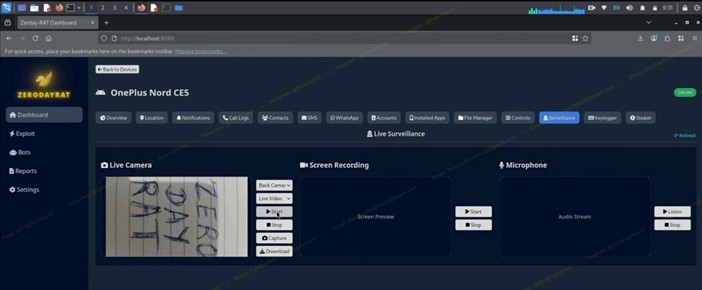
Accessing camera and microphone feeds – Source: iVerify
Credential and OTP interception
With SMS access, ZeroDayRAT can:
- Capture incoming OTPs to bypass 2FA
- Send SMS messages from the victim’s device for fraud or malware distribution
A keylogging module collects:
- Passwords
- Gestures
- Screen unlock patterns
- Other sensitive input
Financial theft modules
ZeroDayRAT includes dedicated modules for cryptocurrency and banking apps.
Crypto stealer:
- Scans for wallet apps (MetaMask, Trust Wallet, Binance, Coinbase, etc.)
- Logs wallet IDs and balances
- Performs clipboard address injection
Bank/payment stealer:
- Targets banking and payment apps including UPI platforms and Apple Pay/PayPal
- Uses overlay attacks to steal credentials via fake screens
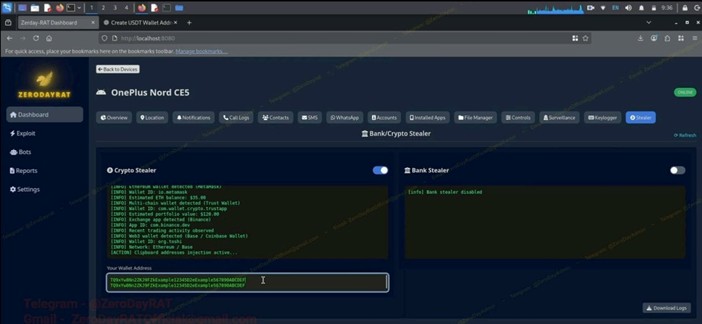
The crypto and bank stealer modules – Source: iVerify
iVerify notes that while delivery methods are still being investigated, ZeroDayRAT functions as a complete mobile compromise toolkit once installed.
Why is it noteworthy?
ZeroDayRAT enables deep, persistent compromise across both major mobile platforms, combining surveillance, device control, credential theft, and financial fraud in a single package. With support for a wide range of OS versions, it allows attackers to monitor communications, account activity, app data, and location history—all from an easy-to-use operator dashboard.
Its built‑in financial theft capabilities, including crypto wallet scanning and banking app overlays, indicate that ZeroDayRAT is designed not just for surveillance, but for direct monetization. By intercepting OTPs and keylogging credentials, it can even bypass 2FA/MFA protections.
What is the exposure or risk?
Risk increases significantly when devices install apps from untrusted sources or are used for sensitive activities such as mobile banking, payments, accessing corporate accounts, or handling confidential data.
A compromised device can expose:
- SMS messages, notifications, and app data
- Photos, files, and personal media
- GPS location, audio, and camera feeds
- Banking credentials, cryptocurrency transfers, and payment app sessions
For organizations, an infected employee device may leak:
- Corporate email
- Collaboration data
- VPN, SSO, or identity credentials
This can allow attackers to move laterally into internal systems or cloud environments—even if core infrastructure is secure.
What are the recommendations?
Barracuda recommends the following steps to secure your mobile devices:
- Keeping Android and iOS fully updated with the latest security patches.
- Restricting app sources to official stores and reputable publishers.
- Avoid clicking links in unsolicited SMS messages (“smishing”)
- Be wary of app downloads shared via messaging apps like WhatsApp and Telegram
- Using platform‑level protections such as iOS Lockdown Mode and Android Advanced Protection for high‑risk users.
- Applying MDM/UEM policies, least‑privilege permissions, and regular app reviews in organizational environments.
References
For more in-depth information about the recommendations, please visit the following links:
- https://www.bleepingcomputer.com/news/security/zerodayrat-malware-grants-full-access-to-android-ios-devices/
- https://iverify.io/blog/breaking-down-zerodayrat—new-spyware-targeting-android-and-ios
If you have any questions about this Cybersecurity Threat Advisory, don’t hesitate to get in touch with Barracuda Managed XDR’s Security Operations Center.
This post originally appeared on Smarter MSP.

